BLACK SHADES CRYPTO RANSOMEWARE
A new ransomware called Black Shades Crypter was discovere that encrypts your data and ransoms it for very low price of $30 paid in bitcoins or Paypal. This ransom targets both English and Russian speaking victim's as note also contains russian language it converts any file to .silent extension and encrypts files.
Unlikely, this ransomware includes strings in the executable that contain taunting messages to security researchers who may be analyzing the ransomware.Unfortunately, at this time there is no way to decrypt this ransomware for free.
Black Shades Crypter Taunts Security Researchers
When analyzing the Black Shades ransomware there are multiple obfuscated strings in the source code that appear to be taunting security researchers who are analyzing it. Some of these strings are simply base64 encoded, while two others use basic string manipulation that is easily decoded.
The obfuscated strings that were found are shown below:
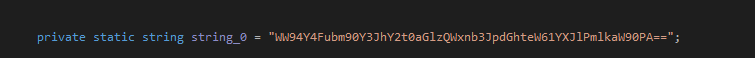
The above strings translates to: YoxcnnotcrackthisAlgorithmynare>idiot<
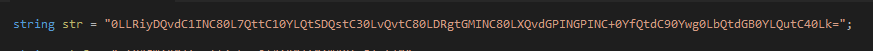
This decodes to the Russian String: вы не можете взломать меня я очень жесткий
In English (Google Translated. I can't make this stuff up): you can not hack me, I am very hard
In English (Google Translated. I can't make this stuff up): you can not hack me, I am very hard
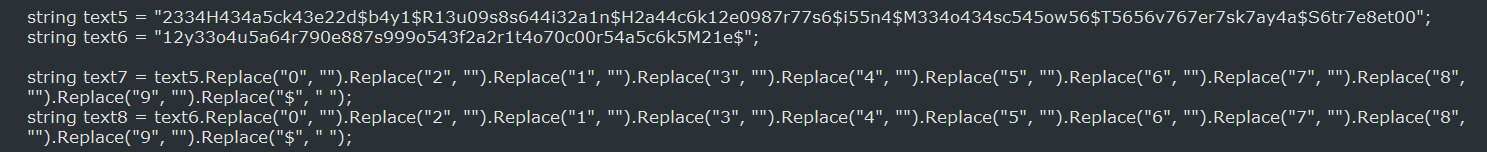
Text5 decodes to: Hacked by Russian Hackers in Moscow Tverskaya Street
Text6 decodes to: youaresofartocrackMe
Text6 decodes to: youaresofartocrackMe
The Black Shades Crypter Encryption Process
It is currently unknown how the Black Shades Ransomware is being distributed,
but based on the string YouTube embedded in executable,MalwareHunterTeam thinks it may be distributed as fake videos, fake cracks, or fake patches.Once executed, Black Shades will delete the Shadow Volume Copies on the computer using this command:
but based on the string YouTube embedded in executable,MalwareHunterTeam thinks it may be distributed as fake videos, fake cracks, or fake patches.Once executed, Black Shades will delete the Shadow Volume Copies on the computer using this command:
cmd.exe /C vssadmin.exe Delete Shadows /All /Quiet
It will then determine the victim's IP address by going to the site http://icanhazip.com and to see if there is an Internet connection by going to Google.com. If the program cannot connect to icanhazip.com it will crash and display the below error. This means that you can modify your hosts file and point icanhazip.com to 127.0.0.1 to block this ransomware from encrypting a computer.
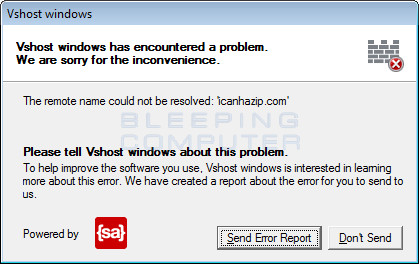
It will then create a unique ID for the victim and check to see if it can connect to Google. If it is able to, it will upload it along with the computer name, user name, key, execution time, the number 0 to act as a placeholder for the amount of files encrypted, and a reference string to the Command & Control server. This reference string is currently set to Youtube.
When encrypting a victim's computer, Black Shades will only encrypt the following folders on the C: drive using AES-256 encryption and also drop a file in each folder called YourID.txt, which contains the unique victim ID. When encrypting the Desktop it will also drop the Ваш идентификатор file, which contains the victim ID as well.
%Userprofile%\Downloads
%Userprofile%\Documents
%Userprofile%\Desktop
%Userprofile%\Pictures
%Userprofile%\Music
%Userprofile%\Videos
C:\Users\Public
On other drives, it will encrypt every folder it scans. When encrypting a file it will append the .silentextension to encrypted files. For example, test.jpg will become test.jpg.silent. When encrypting files it will only encrypt those that have one of the following extensions.
.vb,.cs,.c,.h,.html,.7z,.tar,.gz,.m4a,.wma,.aac,.csv,.rm,.txt,.text,.zip,.rar,.m,.ai,.cs,.db,.nd,.xlsx,.pl,.ps,.py,.3dm,.3ds,.3fr,.3g2,.ini,.xml,.jar,.lz,.mda,.log,.mpeg,.myo,.fon,.gif,.JNG,.jp2,.PC3,.PC2,.PC1,.PNS,.MP2,.AAC,.3gp,.ach,.arw,.asf,.asx,.avi,.bak,.bay,.mpg,.mpe,.swf,.PPJ,.cdr,.cer,.cpp,.cr2,.crt,.crw,.dbf,.dcr,.html,.xhtml,.mhtml,.asp,.dds,.der,.des,.dng,.doc,.dtd,.dwg,.dxf,.CSS,.rss,.jsp,.php,.dxg,.eml,.eps,.ert,.fla,.fla,.flv,.hpp,.docm,.docx,.flac,.iif,.ipe,.ipg,.kdc,.key,.lua,.m4v,.max,.xls,.yuv,.back,.mdb,.mdf,.mef,.mov,.mp3,.mp4,.mpg,.mrw,.x3f,.xlk,.xlr,.msg,.nef,.nk2,.nrw,.oab,.obi,.odb,.odc,.wmv,.wpd,.wps,.odm,.odp,.ods,.odt,.orf,.ost,.p12,.p7b,.vob,.wav,.wb2,.p7c,.pab,.pas,.pct,.pdb,.pdd,.pdf,.per,.sr2,.srf,.str,.ar,.bz2,.rz,.s7z,.apk,.zipx,.pem,.pfx,.pps,.ppt,.prf,.psd,.pst,.ptx,.rw2,.rwl,.sql,.3gp,.qba,.qbb,.qbm,.qbr,.qbw,.qbx,.qby,.r3d,.raf,.raw,.rtf,.AVI,.indd,.java,.jpeg,.pptm,.pptx,.xlsb,.xlsm,.jpg,.png,.ico,.JPG,.MP4,.MP4,.FLV,.MKV,
During different stages of the encryption process it will check again for the ability to connect to Google, and if possible, will connect to the Command & Control server and send an update that contains the count of files that have been encrypted.
When done encrypting, Black Shades will create the Hacked_Read_me_to_decrypt_files.Htmlransom note on the Windows Desktop and also copy it into the victim's startup folder so that it shows every time the user logs into the computer.
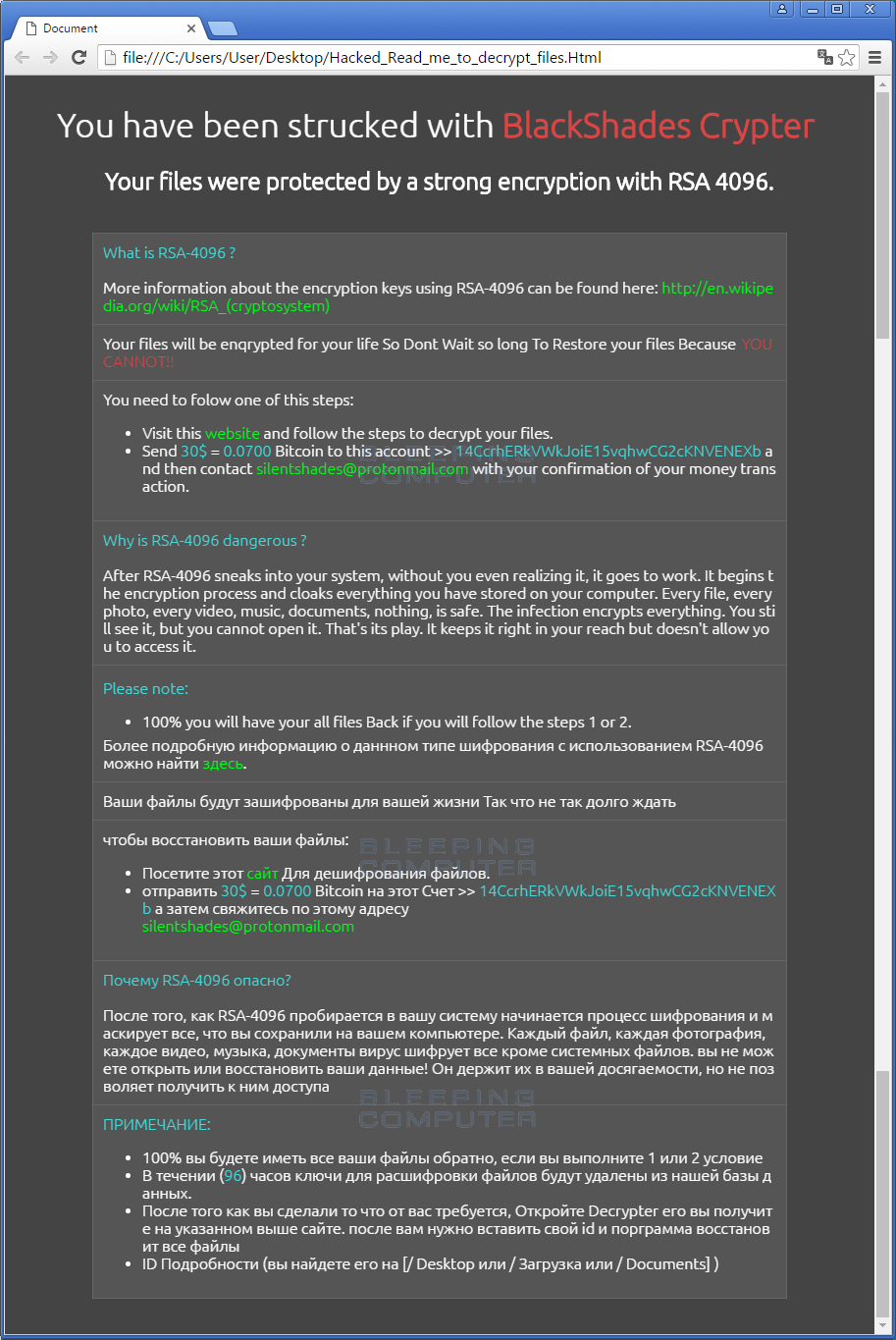
This ransom note contains instructions on how to connect to the associated payment site, which is described below.
When this whole process is completed, Black Shades will try to delete itself and leave behind only the ransom notes.
The Black Shades File Decrypter Site
The Black Shades Ransom note contain a link to the payment site where a victim can pay the ransom. This site is titled the Black Shades File Decrypter and allows a victim to make a payment in bitcoins or using Paypal.
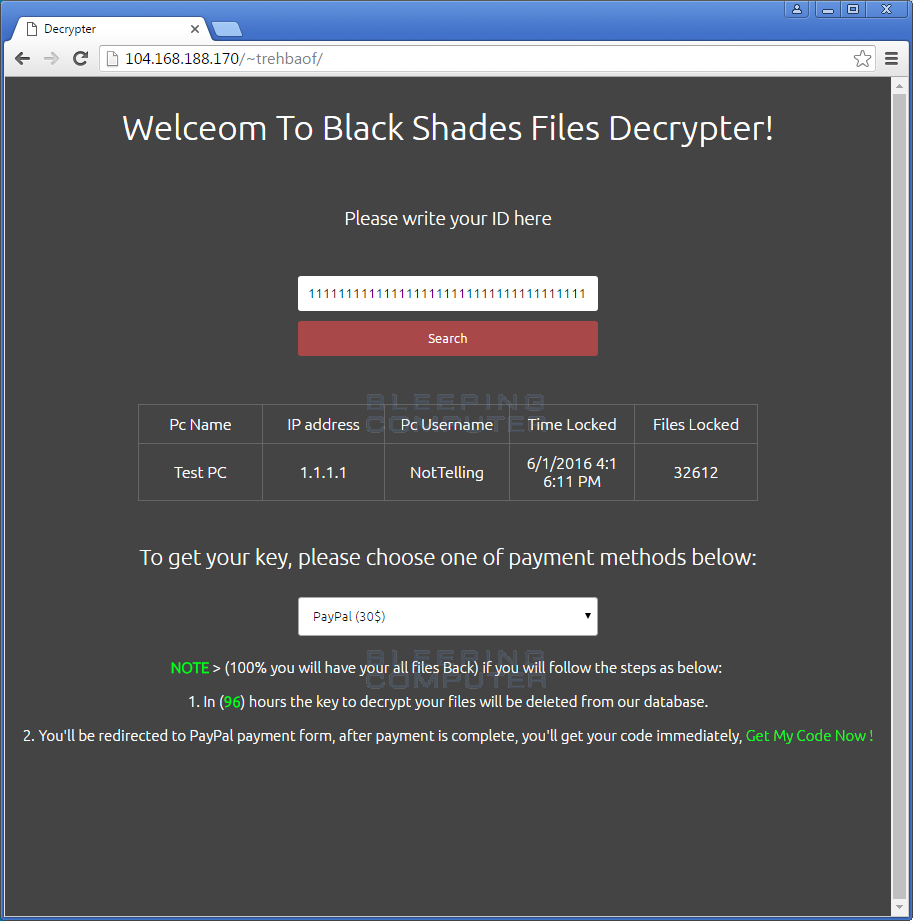
The use of Paypal is an odd choice for any criminal activity as it can easily be traced.
Updates:
6/3/16 - MalwareHunterTeam pointed out that not being able to connect to http://icanhazip.com will generate a crash. Also realized that Google connection is only for checking if connected to the Internet.
Files associated with the Black Shades Crypter Ransomware:
%UserProfile%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\win.exe
%UserProfile%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Hacked_Read_me_to_decrypt_files.Html
%UserProfile%\AppData\Roaming\Windows\win.exe
YourID.txt
Ваш идентификатор
Hacked_Read_me_to_decrypt_files.Html
Registry Entries associated with the Black Shades Crypter Ransomware::
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Driver"="%UserProfile%\AppData\Roaming\Windows\win.exe" /autostart"
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore\Setup\Generalize "DisableSR" = 1
HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = 1